The Ransomware Evolution


From theoretical possibility to a thriving criminal enterprise, ransomware has come a long way. Read on to know more:
According to a recent survey, ransomware payments have nearly doubled $1.5 million over the past year, with the highest-earning organisations the most likely to pay attackers. These ransomware attacks, characterised by hackers encrypting sensitive data and demanding ransoms for its release, have become increasingly common and sophisticated, affecting governments, businesses, and individuals alike and posing an emerging threat to cryptocurrencies, particularly Ethereum.
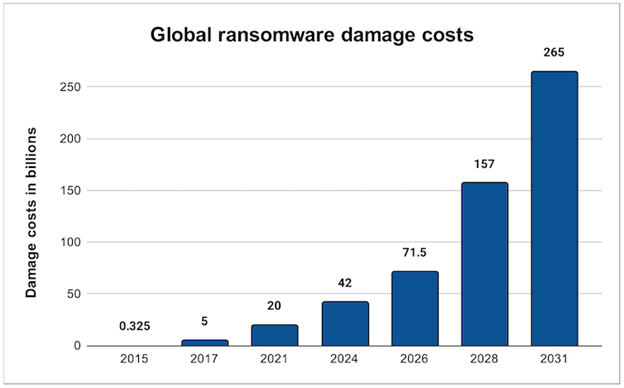
Figure 1: Global ransomware damage costs and forecasts; Source: World Economic Forum/The Conversation
The Proliferation of Ransomware
Ransomware attacks have become so frequent that they often fail to make significant headlines. However, exceptions occur, such as the May and June 2023 attack exploiting a vulnerability in the Moveit file transfer app, which garnered widespread attention due to its high-profile victims, including British Airways, the BBC, and Boots. This alarming trend is exemplified by the fact that the average ransomware payment by UK organisations in 2023 was even higher, at US$2.1 million.
The National Cyber Security Centre (NCSC) in the UK thus issued new guidance in 2022, urging organisations to bolster their cybersecurity defences amid concerns of state-sponsored cyberattacks linked to the conflict in Ukraine. These attacks, frequently involving Russia, have highlighted the geopolitical implications of ransomware.
Ransomware attacks can have diverse and severe financial and societal impacts, affecting various sectors, including government, healthcare, education, and small businesses. The May 2023 Dallas City Government attack, for instance, disrupted hearings, trials, and jury duty, leading to the closure of the Dallas Municipal Court Building. It indirectly affected police activities and summer youth programs due to stretched resources. The threat of publishing sensitive data, including personal information, court cases, prisoner identities, and government documents, added to the gravity of the situation.
The Royal Mail in the UK experienced a ransomware attack in January 2023, resulting in the suspension of international deliveries for over a month. This not only affected the organisation’s revenue and reputation but also had widespread repercussions on small businesses and individuals relying on its services. Similarly, the Irish NHS fell victim to a ransomware attack in May 2021, leading to appointment cancellations and potential financial losses of up to 100 million euros.
Education has also become a prime target, with schools facing threats to publish sensitive data, including safeguarding reports and information about vulnerable children. Timed attacks, like the one on a school in Dorchester, UK, during the main exam period in June 2023, negatively impact children’s well-being and educational achievement. Many ransomware attacks specifically target small businesses and charities, causing devastating consequences, including business disruption, lost reputation, and layoffs.
The Evolution of Ransomware
The origins of ransomware can be traced back to the AIDS or PC Cyborg Trojan virus in the 1980s. Victims who inserted a floppy disk into their computers found their files encrypted, with a ransom demand following. The infamous CryptoLocker attack in 2013 and 2014 marked a turning point in ransomware’s evolution, as it was the first mass-distributed, technically sound ransomware. Criminals realised the potential for substantial profits through ransomware.
Ransomware-as-a-service (RaaS) emerged, enabling cybercriminals to obtain and use pre-made ransomware without advanced technical skills. The dark web provided an ideal platform for this, and it became a hub for cybercriminals to communicate, exchange illegal goods and services, and transact in cryptocurrencies. The barriers to entry for cybercriminals were lowered, increasing the number of attacks.
Ransomware attacks transitioned from mass phishing campaigns to more targeted assaults on organisations with the financial capability to pay significant ransoms. This shift included multinational corporations, legal firms, schools, universities, hospitals, and healthcare providers. The emergence of double extortion threats further escalated the sophistication of ransomware attacks. Criminals began exfiltrating data in addition to encrypting it, providing them with leverage to demand ransoms for both decryption and data non-disclosure.
The Role of Cryptocurrencies in Ransomware
Cryptocurrencies have played a central role in the evolution of ransomware, as they enable criminals to receive ransom payments with a degree of anonymity and efficiency not achievable through traditional banking channels. However, as cryptocurrencies have evolved, so have the tactics of ransomware groups.
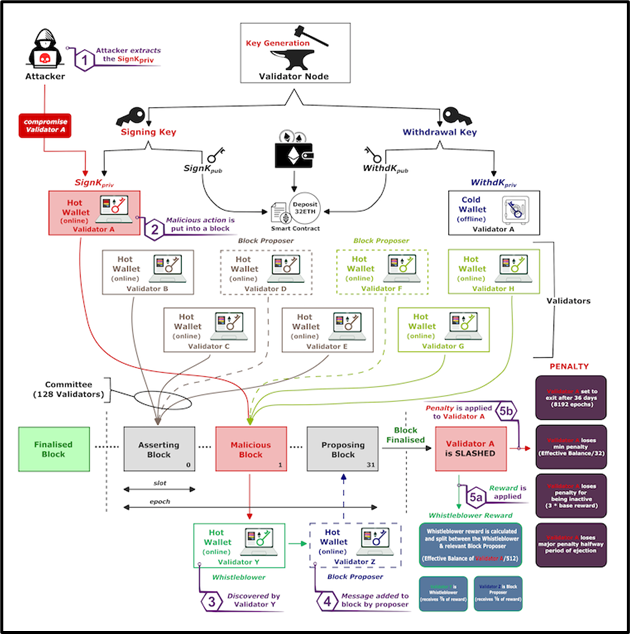
Figure 2: Slashing; Source: World Economic Forum/The Conversation
Proof-of-stake (PoS) cryptocurrencies, such as Ethereum, have gained prominence as an energy-efficient alternative to proof-of-work (PoW) mechanisms. PoS relies on validators who stake a significant amount of the cryptocurrency to validate transactions. This staked money presents a novel threat to PoS cryptocurrencies, as criminals could exploit validators through a process known as “slashing.” Slashing penalises malicious actions by validators, resulting in financial losses and removal from the network.
Attackers who gain access to validator signing keys could blackmail victims into paying ransoms to prevent slashing. To ensure that victims receive what they pay for, smart contracts have been proposed as a means to guarantee the release of decryption keys once the ransom is paid. These smart contracts act as escrow systems and ensure that both parties uphold their end of the bargain.
However, the extortion threat posed by compromising staking pools, which manage multiple validators, is even more significant. Staking pools are responsible for millions of dollars in stake and, if compromised, could result in ransom demands worth millions of dollars. Proper security measures, such as protecting signing keys, are essential for mitigating this threat.
What next?
Ransomware is here to stay and will remain a significant challenge for years to come. The criminal ecosystem around ransomware continues to adapt, incentivising payments and increasing illicit gains. To combat this threat effectively, greater awareness, investment in cybersecurity, and regulations are necessary. Organisations should focus on securing digital keys and sensitive information to minimise vulnerabilities.
From theoretical possibility to a thriving criminal enterprise, ransomware has come a long way. The emergence of PoS cryptocurrencies introduces new opportunities for extortion, highlighting the need for proactive security measures. As ransomware continues to pose a significant threat to society and cryptocurrency, vigilance and preparedness are essential in mitigating its impact.
Know more about our Top Ranked PGDM in Management, among the Best Management Diploma in Kolkata and West Bengal, with Digital-Ready PGDM with Super-specialization in Business Analytics, PGDM with Super-specialization in Banking and Finance, and PGDM with Super-specialization in Marketing.
